Web
Writeup of a forensic challenge during Imaginary2023 CTF
FORENSIC
~1 minute
FORENSIC(web) - (100pts) - 178 solves
This forensic challenge was a classic in its category. We have access to a mozilla profile tree.
.mozilla/
├── extensions
└── firefox
├── 8ubdbl3q.default
│ ├── addons.json
│ ├── addonStartup.json.lz4
│ ├── AlternateServices.txt
│ ├── bookmarkbackups
│ ├── broadcast-listeners.json
│ ├── cert9.db
│ ├── compatibility.ini
│ ├── containers.json
│ ├── content-prefs.sqlite
│ ├── cookies.sqlite
│ ├── crashes
│ │ ├── events
│ │ └── store.json.mozlz4
│ ├── datareporting
│ │ ├── archived
│ │ │ └── 2023-07
│ │ │ ├── 1688944261467.879ff44e-96ed-49f4-bfe5-3641f1b541d5.new-profile.jsonlz4
│ │ │ ├── 1688944261480.04e2b429-3a94-4b39-bdb7-7c8ed9421339.event.jsonlz4
│ │ │ ├── 1688944261540.0c971cc6-fe25-494a-ac65-2765115705e1.main.jsonlz4
│ │ │ └── 1688944261563.00b704ae-8adc-49b0-aef5-630a602c617e.first-shutdown.jsonlz4
│ │ ├── glean
│ │ │ ├── db
│ │ │ │ └── data.safe.bin
│ │ │ ├── events
│ │ │ │ ├── background-update
│ │ │ │ ├── events
│ │ │ │ └── pageload
│ │ │ ├── pending_pings
│ │ │ │ └── c2
[...]Thanks to : 
i was among the first to flag the challenge. In fact, there's a CLI tool that lets you scrap these mozilla profiles : https://github.com/numirias/firefed
In our firefox folder we preshot and try :
firefed -p 8ubdbl3q.default/ history && firefed -p 8ubdbl3q.default/ logins
Bingo :
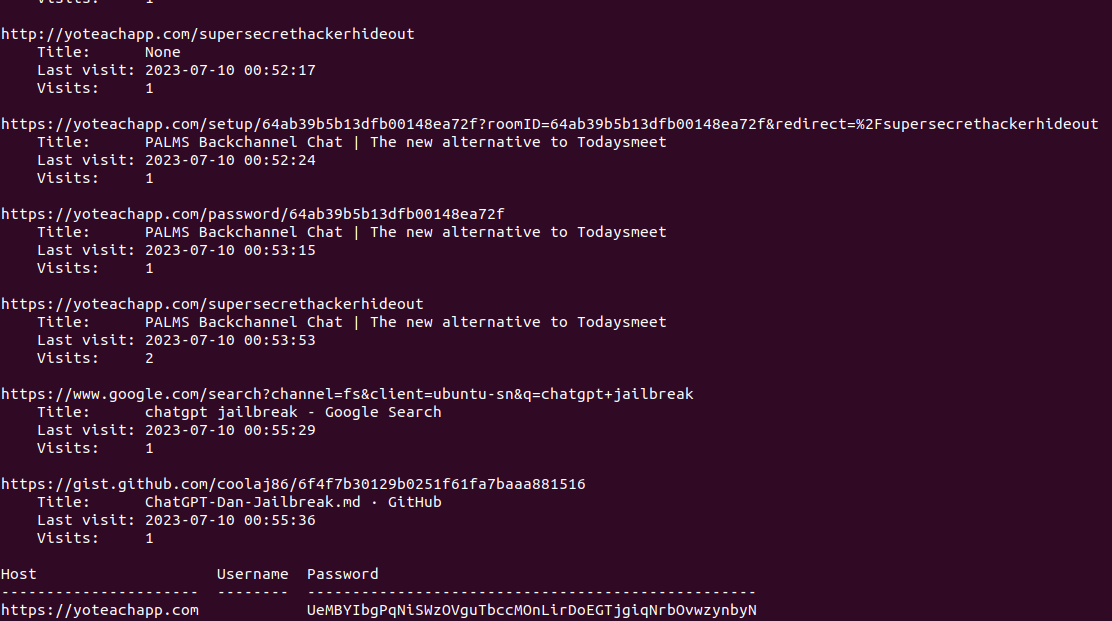
The result is a password:
UeMBYIbgPqNiSWzOVguTbccMOnLirDoEGTjgiqNrbOvwzynbyN
and a multitude of sites :
https://yoteachapp.com/supersecrethackerhideout is the most relevant
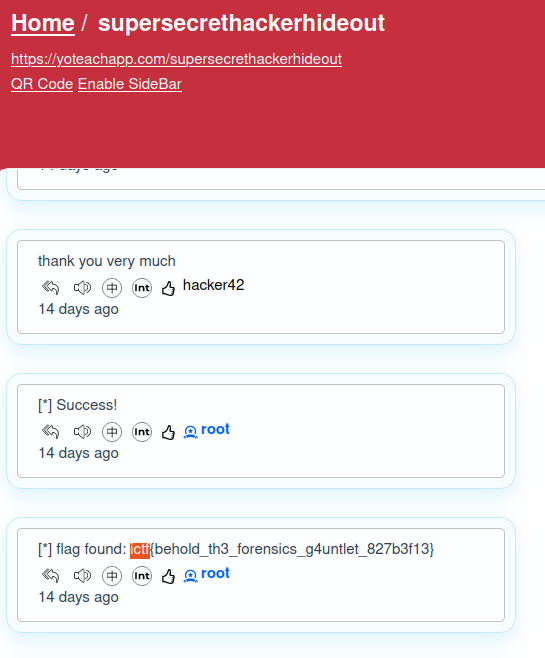
We go to the site, which asks for a password. When we give it, we get a sort of chat with the flag!
ictf{behold_th3_forensics_g4untlet_827b3f13}